#Rijndael Algorithm Decryption
Explore tagged Tumblr posts
Text
C# - Encrypt and Decrypt data using a symmetric key - Rijndael Algorithm
C# – Encrypt and Decrypt data using a symmetric key – Rijndael Algorithm
In this article, we will write a C# program to Encrypt and Decrypt data using a symmetric key
What is Symmetric Key?
Symmetric-key algorithms are algorithms for cryptography that use the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. The keys may be identical or there may be a simple transformation to go between the two keys.
C# Implementation to Encrypt…
View On WordPress
#Rijndael Algorithm C#Rijndael Algorithm Decryption#Rijndael Algorithm Encryption#Symmetric key algorithm#Symmetric key algorithm in C
0 notes
Text
Week_7 // Module_Hwk
1. AES & Block Cipher Modes
Modern Encryption Standards
The modern era of cryptography began in the 70s when the National Bureau of Standards put out a call for a free and public encryption standard. The result was DES - the Data Encryption Standard. The NSA made some tweaks at the time, which we did understand the impact of until two decades later.
By the 90s DES was considered crackable due to its relatively small 56-bit key, and it was quite slow to run in software, so a search for a replacement algorithm began. Many algorithms were submitted, but the winning cipher was one known as Rijndael.
Read the history of modern ciphers, including DES and how AES works, by reading this comic below.
Crypto Terms
Research the following terms and develop an understanding of what they mean:
Confusion: means that each binary digit (bit) of the ciphertext should depend on several parts of the key, obscuring the connections between the two
Diffusion: means that if we change a single bit of the plaintext, then (statistically) half of the bits in the ciphertext should change, and similarly, if we change one bit of the ciphertext, then approximately one-half of the plaintext bits should change
Avalanche Effect: one simple change can lead to a huge difference
SP Boxes
Fiestal Networks: is a symmetric structure used in the construction of block ciphers, named after the German IBM cryptographer Horst Feistel;
Block Ciphers: A block cipher is an encryption method that applies a deterministic algorithm along with a symmetric key to encrypt a block of text, rather than encrypting one bit at a time as in stream ciphers.
Stream Ciphers: is a symmetric key cipher where plaintext digits are combined with a pseudorandom cipher digit stream (keystream).
Block Cipher Modes
ECB - Electronic Code Book - ECB suffers from the problem that the same input will encode to the same output. Making analysis trivial.
CBC - Cipher Block Chaining - it makes encrypting things very slow as it is no longer parallelizable - we need to wait for the previous block to be encrypted before we can start on the next block
CTR - Counter Mode - The result is a cipher mode that doesn't suffer from the problems of ECB, but is also parallelisable in the encryption and decryption stages.
2. Social Engineering simulator
You objective is to use social engineering over email to achieve the following objectives :
Obtain the Facebook login credentials from the Puppy Love organisation Facebook page
Organise for a payment of $1200 to be made to your fake account by the Puppy Love accounts team : BSB : 123456, ACC NO : 12347890
The social engineering can only occur via the email link below. Puppy Love is a fictitious company.
3. Trump Phishing
Craft a phishing email attack aimed at Donald Trump that would succeed in luring Trump into clicking a link in an email.
Post your full email below - do not link to a blog post! (though you may post you answer there as well)
DONAL LOVES HIS TWITTER!
To @realDonaldTrump,
Your request to deactivate your Twitter account has been processed.
If this was not you or if you suspect your account has been hacked, then follow instructions here.
Otherwise, we will miss you!
Staff at Twitter
Automatically generated email, please do not reply.
4. knowledge Based Authentication
http://comp6445-curlybracket-letsmakeflagsgreatagain-curlybracket.bid/challenges/kba/index.html
1 note
·
View note
Text
Macpass security review

Macpass security review windows 10#
Macpass security review software#
In the case of Windows APIs, sometimes, various memory buffers which contain decrypted entries may not be scrubbed correctly. However, errors in workflows permitted the researchers from extracting credential entries which have been interacted with. It is a native OS X port of KeePass, the free. " KeePass scrubs the master password from memory and is not recoverable. MacPass is a free, open-source password manager, which helps you to manage your passwords in a secure way. It was also possible for the researchers to extract the master password and interacted-with password entries due to a memory leak."
Macpass security review software#
However, ISE reported that these entries persist in memory after the software enters a locked state. " LastPass obfuscates the master password while users are typing in the entry, and when the password manager enters an unlocked state, database entries are only decrypted into memory when there is user interaction. Here's what ISE had to say about LastPass and KeePass - two of the most popular password managers available: MacPass is described as A free, open-source, KeePass-compatible password manager for macOS and is a password manager in the security & privacy category. The report has summarized the main findings based on each password management solution. Copilot Packages Security Code review Issues Discussions Integrations GitHub Sponsors Customer stories Team Enterprise Explore Explore GitHub Learn and. It may be possible that malicious programs downloaded to the same machine by threat actors could do the same. ISE was able to extract these passwords and other login credentials from memory while the password manager in question was locked. File format compatibility with KeePass2, KeePassX, MacPass, KeeWeb and many others. In one example, the master password which users need to use to access their cache of credentials was stored in PC RAM in a plaintext, readable format.
Macpass security review windows 10#
The vulnerabilities were found in software operating on Windows 10 systems. The team said that each password management solution "failed to provide the security to safeguard a user's passwords as advertised" and " fundamental flaws" were found that "exposed the data they are designed to protect." The complete database is always encrypted with the AES (alias Rijndael) encryption algorithm using a 256 bit key. Every feature is cross-platform and tested to give users the same feel on each operating system, including the loved auto-type feature. Chiefcrash shares a report from ZDNet: Independent Security Evaluators (ISE) published an assessment on Tuesday with the results of testing with several popular password managers, including LastPass and KeePass. KeePassXC is a community fork of KeePassX, the cross-platform port of KeePass for Windows.

0 notes
Text
File decryption tool keepsafe

#File decryption tool keepsafe android
#File decryption tool keepsafe password
Any reliable antivirus solution can do this for you. Make sure you remove the malware from your system first, otherwise it will repeatedly lock your system or encrypt files. If a correct PIN is given or bruteforce is achieved then the script will move on to decrypting and outputting the media files. IMPORTANT Before downloading and starting the solution, read the how-to guide. Browse privately with a private browser app and VPN. Lock private photos & videos with Photo Vault. If the user chooses not to enter a PIN then the script will attampt to bruteforce it. Each subfolder was named using the first 2 letters of the file, e.g., subfolder 2e stored the encrypted media file 2e3c1f4aa10da568c5a2625145779ad01163acc8. Keepsafe is a family of privacy apps which gives you control to protect your online privacy and personal space. The script will ask the user for the PIN, there is limited validation of the input. Preview will be enabled, once image is completely decrypted. Upload your encrypted image in tool and click on decrypt image button revoke original image visually. The developers also make the following statement: ‘Secret Calculator’s architecture was developed with the help of data security consultants experts to make sure that nobody, including our team, will be able to access your private photo locker without knowing your pass phrase, even if your device is stolen!’ Script Usage Image decryption tool help to restore your encrypted image to its original pixels. Encryption strength AES Rijndael: 256 bit / Hash: SHA-256.
#File decryption tool keepsafe password
Can generate the hash of the source file as password for symmetric encryption. To prevent this from happening in the future, read our 5-step guide to prevent ransomware attacks. File encryption/decryption tools with strongest AES(Rijndael) algorithms. Any reliable antivirus solution will do that for you.
#File decryption tool keepsafe android
ksd file description File extension ksd is also used for the main file typed he KeepSafe, a case sensitive data protection suite for devices with Google Android or Apple iOS operating systems. Make sure you remove the malware from your system first otherwise it will repeatedly lock your system or encrypt your files. ‘Secret Calculator Photo Vault: Hide Keep Safe Lock’ uses ‘Military Grade Encryption AES-256 bit‘ to keep files safe within the application. Files with ksd extension can be be sometimes found as encrypted data files protected by the KeepSafe data encryption app. A python script to decrypt media files encrypted using the Android application ‘Secret Calculator Photo Vault’ ( ).

0 notes
Text
(Very) Basic intro to AES-256 Cipher
AES stands for “Advanced Encryption Standard” and is a specification that has selected the Rijndael cipher as its symmetric key ciphering algorithm. Using AES, a message can be encrypted with a key (like a password) and no one except the key holder can decrypt the message. This is useful for many reasons, but a good example is a password manager that encrypts all of the user’s passwords using one master password. This is how Qvault, our free open-source password manager operates.
Symmetric Encryption vs Asymmetric Encryption
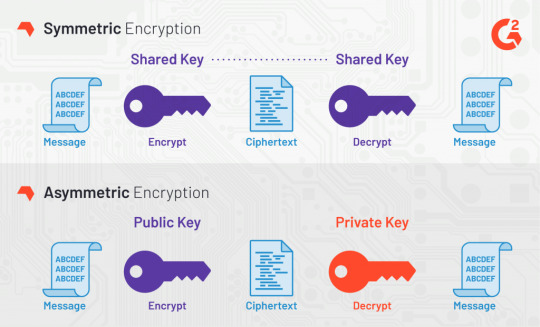
https://learn.g2.com/what-is-encryption
As shown above, symmetric encryption uses the same key for encryption and decryption and asymmetric encryption uses different keys.
Asymmetric encryption is preferred when you want someone to be able to send you encrypted data, but you don’t want to give them your private key.
Symmetric encryption is preferred when you are encrypting only for yourself.

Kullabs
AES-256 Secret Key
The secret key used in AES-256 must be 256 bits long. In order to use a password or passphrase as the key, a hashing algorithm can be used to extend the length.
The shorter the password or passphrase, the easier it is for an attacker to decrypt the data by guessing passwords, hashing them, and attempting to decrypt the message. In order to mitigate this threat, some applications enforce safeguards.
In the case of Qvault, the master password is hashed using the Scrypt algorithm in order to produce the private key. Scrypt is a very slow password-based key derivation function (similar properties to a hashing algorithm), which slows down attacks. Qvault also requires that passwords are at least 12 characters long, or encourages that users use a passphrase instead.

https://xkcd.com/936/
Rijndael Encryption Process (Simplified)
1. Choose a password, then derive a short key from that password (using a function like Scrypt or SHA-256). This short key will then be expanded using a key schedule to get separate “round keys” for each round of AES-256.
password: password12345678 → short key: aafeeba6959ebeeb96519d5dcf0bcc069f81e4bb56c246d04872db92666e6d4b → first round key: a567fb105ffd90cb
Deriving the round keys from the short key is out of the scope of this article. The important thing for us to understand is that a password is converted into round keys which are used in the AES ciphering process.
2. Choose a secret message:
Here is a secret
3. Encode the first round key and message in hexadecimal bytes and format them in 4×4 tables (top to bottom, left to right):
First Round Key:
61 66 35 39 35 62 66 30 36 31 66 63 37 30 64 62
Message:
48 20 61 63 65 69 20 72 72 73 73 65 65 20 65 74
4. Add the round key to the message (XOR). The corresponding cells in the message and key tables are added together. The output matrix will be used in the next step.
61 ⊕ 48 = 29
35 ⊕ 65 = 50
…etc
29 46 54 5a 50 0b 46 42 44 42 15 06 52 10 01 16
5. In the resulting table, use the substitution box to change each 2-character byte to its corresponding byte:

https://www.researchgate.net/figure/Rijndael-S-box-S-RD_fig7_325428613
a5 5a 20 be 53 2b 5a 2c 1b 2c 59 6f 00 7c 7c 47
6. Shift rows. The first row doesn’t shift, the second-row shifts once, the third row twice, and the last row 3 times.
a5 5a 20 be 53 2b 5a 2c → 2b 5a 2c 53 1b 2c 59 6f → 2c 59 6f 1b → 59 6f 1b 2c 00 7c 7c 47 → 7c 7c 47 00 → 7c 47 00 7c → 47 00 7c 7c
a5 5a 20 be 2b 5a 2c 53 59 6f 1b 2c 47 00 7c 7c
7. Mix Columns. Each column is modulo multiplied by the Rijndael’s Galois Field. The math involved is outside the scope of this article, so I won’t be including the example output matrix.
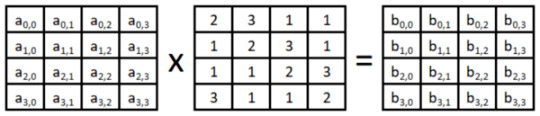
https://www.commonlounge.com/discussion/e32fdd267aaa4240a4464723bc74d0a5
8. The output of the multiplication is used as the input “message” in the next round of AES. Each step is repeated 10 or more times in total, with one extra “add key” step at the end. Each round of “Add key” will use a new round key, but each new round key is still derived from the same password and short key.
Add key
Substitute bytes
Shift rows
Multiply columns
That’s it! /s
Obviously the Rijndael cipher used in AES is fairly complex but I hope I’ve been able to shed light on a high-level view of what goes on inside! Thanks for reading.
Be sure to checkout Qvault, it’s an open-source password manager that uses AES-256 as the cipher.
Sources
https://www.tutorialspoint.com/cryptography/advanced_encryption_standard.htm
https://crypto.stackexchange.com/questions/16125/does-the-secret-key-used-in-aes-have-to-prime
https://en.wikipedia.org/wiki/Scrypt
https://www.samiam.org/galois.html
youtube
Thanks For Reading
Lane on Twitter: @wagslane
Lane on Dev.to: wagslane
Download Qvault: https://qvault.io
Star our Github: https://github.com/q-vault/qvault
The post (Very) Basic intro to AES-256 Cipher appeared first on Qvault.
source https://qvault.io/2020/01/02/very-basic-intro-to-aes-256-cipher/?utm_source=rss&utm_medium=rss&utm_campaign=very-basic-intro-to-aes-256-cipher
0 notes
Text
300+ TOP CISSP Objective Questions and Answers
CISSP Multiple Choice Questions :-
1. When an attacker sends unsolicited communication, it is an example of: A. Spoofing B. Spamming C. Crackers D. Sniffers ANS:- B 2. Masquerading is: A. Attempting to hack a system through backdoors to an operating system or application B. Pretending to be an authorized user C. Always done through IP spoofing D. Applying a subnet mask to an internal IP range ANS:- B 3. Integrity is protection of data from all of the following EXCEPT: A. Unauthorized changes B. Accidental changes C. Data analysis D. Intentional manipulation ANS:- C 4. A security program cannot address which of the following business goals? A. Accuracy of information B. Change control C. User expectations D. Prevention of fraud ANS:- A 5. In most cases, integrity is enforced through : A. Physical security B. Logical security C. Confidentiality D. Access controls ANS:- D 6. A “well-formed transaction” is one that: A. Has all the necessary paperwork to substantiate the transaction. B. Is based on clear business objectives. C. Ensures that data can be manipulated only by a specific set of programs. D. Is subject to duplicate processing. ANS:- C 7. In an accounting department, several people are required to complete a financial process. This is most likely an example of: A. Segregation of duties B. Rotation of duties C. Need-to-know D. Collusion ANS:- A 8. Risk Management is commonly understood as all of the following EXCEPT: A. Analyzing and assessing risk B. Identifying risk C. Accepting or mitigation of risk D. Likelihood of a risk occurring ANS:- D 9. The percentage or degree of damage inflicted on an asset used in the calculation of single loss expectancy can be referred to as: A. Exposure Factor (EF) B. Annualized Rate of Occurrence (ARO) C. Vulnerability D. Likelihood ANS:- A 10. The absence of a fire-suppression system would be best characterized as a(n): A. Exposure B. Threat C. Vulnerability D. Risk ANS:- C

CISSP MCQs 11. Risk Assessment includes all of the following EXCEPT: A. Implementation of effective countermeasures B. Ensuring that risk is managed C. Analysis of the current state of security in the target environment D. Strategic analysis of risk ANS:- A 12. A risk management project may be subject to overlooking certain types of threats. What can assist the risk management team to prevent that? A. Automated tools B. Adoption of qualitative risk assessment processes C. Increased reliance on internal experts for risk assessment D. Recalculation of the work factor ANS:- A 13. Data classification can assist an organization in: A. Eliminating regulatory mandates B. Lowering accountability of data classifiers C. Reducing costs for protecting data D. Normalization of databases ANS:- C 14. Who “owns” an organization’s data? A. Information technology group B. Users C. Data custodians D. Business units ANS:- D 15. An information security policy does NOT usually include: A. Authority for information security department B. Guidelines for how to implement policy C. Basis for data classification D. Recognition of information as an asset of the organization ANS:- B 16. The role of an information custodian should NOT include: A. Restoration of lost or corrupted data B. Regular backups of data C. Establishing retention periods for data D. Ensuring the availability of data ANS:- C 17. A main objective of awareness training is: A. Provide understanding of responsibilities B. Entertaining the users through creative programs C. Overcoming all resistance to security procedures D. To be repetitive to ensure accountability ANS:- A 18. What is a primary target of a person employing social engineering? A. An individual B. A policy C. Government agencies D. An information system ANS:- A 19. Social engineering can take many forms EXCEPT: A. Dumpster diving B. Coercion or intimidation C. Sympathy D. Eavesdropping ANS:- D 20. Incident response planning can be instrumental in: A. Meeting regulatory requirements B. Creating customer loyalty C. Reducing the impact of an adverse event on the organization D. Ensuring management makes the correct decisions in a crisis ANS:- C CISSP Objective type Questions with Answers 31) Asymmetric key cryptography is used for all of the following except: A. Encryption of data B. Access control C. Nonrepudiation D. Steganography ANS:- D 32) The most common forms of asymmetric key cryptography include A. Diffie–Hellman B. Rijndael C. Blowfish D. SHA-256 ANS:- A 33) What is an important disadvantage of using a public key algorithm compared to a symmetric algorithm? A. A symmetric algorithm provides better access control. B. A symmetric algorithm is a faster process. C. A symmetric algorithm provides nonrepudiation of delivery. D. A symmetric algorithm is more difficult to implement. ANS:- B 34) When a user needs to provide message integrity, what options may be best? A. Send a digital signature of the message to the recipient B. Encrypt the message with a symmetric algorithm and send it C. Encrypt the message with a private key so the recipient can decrypt with the corresponding public key D. Create a checksum, append it to the message, encrypt the message, then send to recipient. ANS:- D 35) A certificate authority provides what benefits to a user? A. Protection of public keys of all users B. History of symmetric keys C. Proof of nonrepudiation of origin D. Validation that a public key is associated with a particular user ANS:- D 36) What is the output length of a RIPEMD-160 hash? A. 160 bits B. 150 bits C. 128 bits D. 104 bits ANS:- A 37) ANSI X9.17 is concerned primarily with A. Protection and secrecy of keys B. Financial records and retention of encrypted data C. Formalizing a key hierarchy D. The lifespan of key-encrypting keys (KKMs) ANS:- A 38) When a certificate is revoked, what is the proper procedure? A. Setting new key expiry dates B. Updating the certificate revocation list C. Removal of the private key from all directories D. Notification to all employees of revoked keys ANS:- B 39) What is not true about link encryption? A. Link encryption encrypts routing information. B. Link encryption is often used for Frame Relay or satellite links. C. Link encryption is suitable for high-risk environments. D. Link encryption provides better traffic flow confidentiality. ANS:- C 40) A_________ is the sequence that controls the operation of the cryptographic algorithm . A. Encoder B. Decoder wheel C. Cryptovariable D. Cryptographic routine ANS:- C 41) The process used in most block ciphers to increase their strength is A. Diffusion B. Confusion C. Step function D. SP-network ANS:- D 42) The two methods of encrypting data are A. Substitution and transposition B. Block and stream C. Symmetric and asymmetric D. DES and AES ANS:- C 43) Cryptography supports all of the core principles of information security except A. Availability B. Confidentiality C. Integrity D. Authenticity ANS:- D 44) A way to defeat frequency analysis as a method to determine the key is to use A. Substitution ciphers B. Transposition ciphers C. Polyalphabetic ciphers D. Inversion ciphers ANS:- C 45) The running key cipher is based on A. Modular arithmetic B. XOR mathematics C. Factoring D. Exponentiation ANS:- A 46) The only cipher system said to be unbreakable by brute force is A. AES B. DES C. One-time pad D. Triple DES ANS:- C 47) Messages protected by steganography can be transmitted to A. Picture files B. Music files C. Video files D. All of the above ANS:- D 48) a significant action has a state that enables actions on an ADP system to be traced to individuals who may then be held responsible. The action does NOT include : A. Violations of security policy. B. Attempted violations of security policy. C. Non-violations of security policy. D. Attempted violations of allowed actions. ANS:- D 49) Which of the following embodies all the detailed actions that personnel are required to follow? A. Standards B. Guidelines C. Procedures D. Baselines ANS:- C 50) which of the following choices is NOT part of a security policy? A. definition of overall steps of information security and the importance of security B. statement of management intend, supporting the goals and principles of information security C. definition of general and specific responsibilities for information security management D. .description of specific technologies used in the field of information security ANS:- D CISSP Questions and Answers pdf Download Read the full article
0 notes
Text
Advanced Encryption Standard (AES)
AES is also known as by is original name Rijndael after its developers Vincent Rijmen and John Daemen. AES is a block cipher that uses a 128-bit block known as the state. The state is organised as a 32*32 bit array (or a 4*4 bytes). It goes through 10 rounds of encryption. The key for AES has multiple key lengths for greater security but worse performance. The key lengths are 128, 192 and 256-bits. Most computers and specialised hardware to use AES.
Method
Key Expansion - derives the round keys from the using Rijndael’s key schedule from the main key, so each round has a 128 bit round key. This is done at the beginning and not every round.
Substitute Bytes - Each byte in the state is substituted by using a look-up table of a Rijndael s-box. This create confusion in the algorithm relationships.
Shift Rows - each element in the state is shifted down a number (of its row) index of column. This is the first step in creating diffusion
Mix Columns - Each byte in a column of the state is mixed up using a function created by Rijndael. This is the second step of diffusion and means that the output from a round depends on output from the previous round. This step is not done in the final round.
Add Round Key - each byte of the state is XORed with its corresponding byte in the round key
click here for an easy to follow description of how AES enciphers a block.
The Key Expansion is the most important step of the cipher because it is the only part of the algorithm that has unknown information to an attacker. The round keys all derive from the main secret key and so are also unknown to an attacker where as the rest of the steps are completely known to an attacker.
Add Round Key
The other functions are still necessary though, because just doing the Add Round is essentially a substitution and XORing more than once would also be redundant and it would be a weak cipher. This is because every byte in a block does not move from its position, so an attacker just has to crack each byte. There are 2^8 possible combinations for a byte of plaintext and 2^8 possible bytes for the plaintext too and 16 (i.e. 2^4) bytes in a block, therefore to brute force 1 block it would take 19 bits of work ( 2^8 * 2^8 * 2^4 /2 = 2^19) on average. As the average desktop computer can do 31-bits of work a second, so it could crack the average e-mail (75KB or 2^12 blocks) encrypted like this in a second.
Mix Columns and Shift Rows
The Mix Columns function creates makes each byte in a column dependent on each other so an attacker cannot treat the 128-bit block as 16 independent bytes but rather as 4 32-bit blocks.
The Shift Rows function mixes the bytes of each column so an attacker cannot treat a 128-bit block as 4 32-bit blocks as each byte of a column would only depend on the other bytes in its column. So instead of needed to brute force a 128-bit key, an attacker would just need to brute-force 4 (i.e. 2^2) 32-bit keys, which is only 33-bits of work (2^32 * 2^2 / 2 = 2^33). An average desktop would be able to crack a block in a few seconds.
So these two functions working together ensure that to brute force AES, an attacker needs to do 127-bits of work (128-bit key).
Substitute Bytes
Having this function ensure the cipher is no longer a linear/Affine transformation. If the cipher was affine then it could be represented in the form c = Ap + k, where c = cipher text (128 size vector), p = plain text (128 size vector), A = 128*128 matrix and k is a constant that depends on the key. The matrix A is dependent on the shift rows and mix columns functions, both of which are known to everyone and can therefore be pre-calculated. If an attacker can then crack one cipher text block by guessing the plaintext then k can be calculated because k = c - Ap. (e.g. the cipher text is an email and the sender’s has the same sign-off like “sent from my iphone” and the attacker can estimate the location of that plaintext in the cipher text, then the attacker has a matching plaintext block and cipher text block)
The Number of Rounds
Increasing the number of rounds AES goes through increases the amount of confusion and diffusion because it goes through more substitution and more shifting and mixing. The 128-bit key uses 10 rounds because there are ways to crack 6 round versions of AES so Rijdael said “We added 4 rounds as a security margin”. The extra 4 rounds also means that the technique used to crack the 6 round version, increasingly expensive.
The reason the 192-bit and 256-bit keys use more rounds is because techniques that can crack the cipher in less than brute force can afford to be less efficient with longer keys. If a technique that can crack the 128-bit key in 100 bits of work (quicker than brute force) and that same technique can crack 10 round 192-bit key in 155-bits of work as well as cracking 10 round 256-bit key in 215 bits of work, although is less efficient at cracking the longer keys, it still increases bits of worked not needed compared to brute force.
Weaknesses
As AES is a symmetric key cipher, it does not scale well as the size of the network increases as n^2 keys are needed to be shared and kept by everyone in the network. This problem can be overcome by using a cipher that uses public-private keys like RSA to encrypt the small key for the AES, reducing the number of keys needed in a network to 2n
There have been some theoretical attacks have been published but they do not reduce the work enough to make it feasible. Some also are not that practical, like needing to know the plaintext to crack the cipher-text, which could be useful if you want prove that some else received the same file or two users repeatedly use the same key and you had the plain text of one of the messages.
Considering there have been a number of theoretical break, it is probably a good idea to start looking for a new algorithm to encrypt and decrypt now, because it is uncertain how quickly more advances will be discovered.
Common Uses
It was chosen by the NIST as the new standard for encryption after DES. It is therefore used by all US federal government departments. The NSA has approved the 128, 192 or 256-bit keys for “secret” level information but only the 192 or 256-bit keys for “top secret” level information. The reason for using the longer keys for top secret seems to be to protect against a partially known key.
As the longer the key is, the more work an attacker still has to do to crack the rest of the key because if an attacker knew 64-bits of the key, they would still have to over 127-bits of work for the 192-bit and 256-bit keys.
Sources
https://csrc.nist.gov/csrc/media/projects/cryptographic-standards-and-guidelines/documents/aes-development/rijndael-ammended.pdf
https://www.openlearning.com/courses/securityengineering19t2/modules/7/aes/
https://searchsecurity.techtarget.com/definition/Advanced-Encryption-Standard
https://www.eetimes.com/document.asp?doc_id=1279619
https://en.wikipedia.org/wiki/Advanced_Encryption_Standard
https://eprint.iacr.org/2011/449.pdf
https://www.nist.gov/publications/advanced-encryption-standard-aes
http://www.moserware.com/2009/09/stick-figure-guide-to-advanced.html
https://medium.com/@weblab_tech/encrypted-client-server-communication-protection-of-privacy-and-integrity-with-aes-and-rsa-in-c7b180fe614e
https://www.quora.com/What-is-todays-average-computer-processing-speed
https://crypto.stackexchange.com/questions/20228/consequences-of-aes-without-any-one-of-its-operations
https://en.wikipedia.org/wiki/Rijndael_key_schedule
https://en.wikipedia.org/wiki/Rijndael_S-box
https://en.wikipedia.org/wiki/Rijndael_MixColumns
https://crypto.stackexchange.com/questions/2648/how-were-the-number-of-rounds-for-different-key-sizes-of-aes-selected
https://csrc.nist.gov/csrc/media/projects/cryptographic-standards-and-guidelines/documents/aes-development/rijndael-ammended.pdf
0 notes
Text
Crypto Terms
Confusion - a property of the operation of a secure cipher. Refers to making the relationship between the key and the ciphertext as complex and involved as possible.
Diffusion - a property of the operation of a secure cipher. Refers to the property that the redundancy in the statistics of the plaintext is “dissipated” in the statistics of the ciphertext. I.e. the output bits should depend on the input bits in a very complex way.
Avalanche Effect - A desirable proprty of cryptographic algorithms, typically block ciphers and cryptographic hash functions. The avalanche effect is evidence if the output bits change significantly even for a minute change in the input bits.
SP Boxes - Substitution-Permutation network is a series of linked mathematical operations used in block cipher algorithsm e.g. AES (Rijndael). The network takes a block of the plaintext and the key as inputs, and applies several alternating layers of substitution boxes and permutation boxes to produce the ciphertext block.
An S-box substitutes a small block of bits (the input of the S box) by another block of bits (output). A good S-box has the avalanche effect. A P-box is a permutation of all the bits. It takes the outputs of all the S-boxes of one round/layer, permutes the bits and feeds them into the S-boxes of the next round. A good P-box has the property that the output bits of any S-box are distributed to as many S-box inputs as possible.
Feistal Networks - A Feistal cipher (commonly known as Feistal Network) is a symmetric structure used in the construction of block ciphers. It is an iterated cipher with an internal function called a round function. Encryption and decryption operations are very similar, even identical in some cases, requiring only a reversal of the key schedule.
Block Ciphers - Symmetric key ciphers operation on fixed-length groups of bits, called blocks, with an unvarying transformation. It might take a 128-bit block of plaintext as input and output a corresponding 125-bit block of ciphertext. The exact transformation is controlled using a second input which is they key.
Stream Ciphers - Operates on individual digits one at a time, and the transformation varies during the encryption.
0 notes
Text
Week 6: Lecture
This week we learned about:
- AES (Advanced Encryption Standard)
- Block Modes
- ECB (Electronic Codebook Mode)
- CBC (Cipher-Block Chaining)
- CTR (Counter Mode)
- Disk Encryption
- Cryptocurrency
AES (Advanced Encryption Standard)
A symmetric block cipher chosen by the US government to protect classified information and is implemented in software and hardware throughout the world to encrypt sensitive data.
How AES encryption works
AES comprises three block ciphers: AES-128, AES-192 and AES-256. Each cipher encrypts and decrypts data in blocks of 128 bits using cryptographic keys of 128-, 192- and 256-bits, respectively. The Rijndael cipher was designed to accept additional block sizes and key lengths, but for AES, those functions were not adopted.

Symmetric (also known as secret-key) ciphers use the same key for encrypting and decrypting, so the sender and the receiver must both know -- and use -- the same secret key. All key lengths are deemed sufficient to protect classified information up to the "Secret" level with "Top Secret" information requiring either 192- or 256-bit key lengths. There are 10 rounds for 128-bit keys, 12 rounds for 192-bit keys and 14 rounds for 256-bit keys -- a round consists of several processing steps that include substitution, transposition and mixing of the input plaintext and transform it into the final output of ciphertext.
The AES encryption algorithm defines a number of transformations that are to be performed on data stored in an array. The first step of the cipher is to put the data into an array; after which the cipher transformations are repeated over a number of encryption rounds. The number of rounds is determined by the key length, with 10 rounds for 128-bit keys, 12 rounds for 192-bit keys and 14 rounds for 256-bit keys.

The first transformation in the AES encryption cipher is substitution of data using a substitution table; the second transformation shifts data rows, the third mixes columns. The last transformation is a simple exclusive or (XOR) operation performed on each column using a different part of the encryption key -- longer keys need more rounds to complete.
Block Cipher Modes
DES and AES are forms of what is known as a 'block cipher'. This means that for a plain text, they can only encrypt a fixed amount of the file at a time. DES only accepts 64 bits of a plain text at a time and AES supports only 128 bits.
ECB - Electronic Code Book
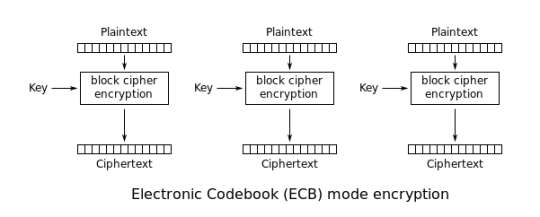
ECB divides the file up into chucks of 128 bits and encrypt them separately.
Flaws: Just like we observed the weaknesses in monoalphabetic substitution ciphers in the early weeks of the course, ECB suffers from the problem that the same input will encode to the same output. Making analysis trivial.
CBC - Cipher Block Chaining
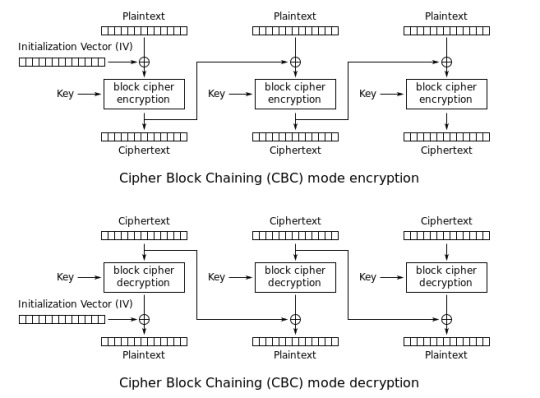
Cipher block chaining attempts to solve the problem of the same blocks resulting in the same cipher text by incorporating the past block in each subsequent block. In that way each block is a result of all the blocks before it.
Since the first block does not have a previous block to include, we use something called an initialisation vector - which is just a. random value which is transferred in the clear alongside the first block.
This prevents the problem that occurs with ECB but unfortunately it makes encrypting things very slow as it is no longer parallelizable - we need to wait for the previous block to be encrypted before we can start on the next block.
CTR - Counter Mode

Counter mode is a bit of a unique mode of encryption that flips most other modes on their heads! Counter mode turns the AES block cipher into a pseudo-stream cipher. Instead of encrypting the plain text, CTR mode encrypts a random NONCE and counter value. For each subsequent block, the counter value is increased, and thanks to the confusion and diffusion properties of AES, a very small change in the plaintext results in a massive change to the cipher text.
This long string of pseudorandom bits is treated like a stream cipher - the actual plaintext is XORed with the output of the encryption of the NONCE and counter, and the real cipher is the result of the XOR operation.
The result is a cipher mode that doesn't suffer from the problems of ECB, but is also parallelisable in the encryption and decryption stages.
0 notes
Text
Week 6 Lecture Reflection
So I wasn’t able to attend the lecture this week due to needing to complete an assignment on that day. In anycase, I took a look at the lecture notes written by students and also the available lecture modules online. I realised that there was a big disconnect between content as in the lecture notes, they were talking about things like Advanced Encryption Standards and Disk Encryption while the video lectures were talking about one time pad and threat modelling.
In anycase, I will try to review and study from both contents as I also haven’t really understood one time pad myself (And many other things due to how poorly I did in the midsem).
Lecture Notes:
Advanced Encryption Standard is a subset of the Rijndael block cipher in which utilises a symmetric key algorithm. It is based on a design principle known as a substitution-permutation network and does not use a Feistel network.
Cannot be broken in feasible time.
A substitution permutation network is a series of linked mathematical operations used in block cipher algorithms. It is where Substituion boxes transform bits into output bits. It will then incorporate a property where changing one input bit will change half o the output bits. In the permutation bits, it will rearrange bits across substituion inputs. Encrypt through substitution boxes and permutation boxes. Key is gained from the boxes and is then combined with bits. Decrypt by inversing S and P boxes and round keys.
Disk Encryption is a technology which protects information by converting it into unreadable code. It generates a random key to encrypt data and stores it in a place that’s not in the disk.
RAM stores data even after shutting off. But if you freeze it, you can slow down data leak. RAM might have encryption key and thus is used to access harddisk.
Extra Lecture notes:
Feistel Ciphers works by splitting the data block into two equal pieces and applies encryption in multiple rounds. Each round implements permutation and combinations derived from the primary function or key.
Smashing the stack for fun and profit - Implementations of possible ways to corrupt the execution stack by writing past the end of an array declared auto in a routine.
Oh man it’s used to create some big bugs.
Video Lecture:
One Time Pad- Literally a key written on a pad and when used and decrypted, is removed and never used again.
It is done by adding the keys (that are usually generated from modulo of something) with the alphabet position of the letter.
Threat Modelling- Need to know where attacks come from because you cant fix all weaknesses but you can minimise the greatest dangers.
Duress Code- Fake Code.
Common Threat Classes- Users, Casual Attackers, Determined attackers, Funded attackers.
0 notes
Text
MasterVault Encryption Toolkit # Encrypt any files and strings (Apps)
19 Algorithms and 9 Hases available Encrypt any type of file or text string Sets encryption passwords Set the name of the encryption extension you want Option to create zip with encrypted files Decryptor DMV.exe is added to the zips Custom comment in zip Custom signature in zip comment Option to include password and encryption type to the zip comment Option to set password to the same zip Generation of a single file ut.ud. (without it you can not decrypt) For text strings it is possible to choose “number of encryption loops” You can also set password for text mode
Algoritmos soportados: BlowFish CAST 128 CAST 256 DES 3 DES ICE Thin ICE ICE 2 IDEA Mars Misty 1 RC2 RC4 RC5 RC6 Rijndael SerPent TEA TwoFish
Hash soportados: Haval MD4 MD5 RMD 128 RMD 160 SHA 1 SHA 384 SHA 512 Tiger
Thanks to this variety of algorithms and hases you have at your reach a very powerful tool. You can combine any algorithm with any hash.
from CodeCanyon new items https://ift.tt/2tYuCrs via IFTTT https://goo.gl/zxKHwc
0 notes
Text
Original Post from Talos Security Author:
Executive summary
Most users assume they are safe when surfing the web on a daily basis. But information-stealing malware can operate in the background of infected systems, looking to steal users’ passwords, track their habits online and hijack personal information.
Cisco Talos has monitored adversaries which are behind a wave of ongoing campaigns dropping well-known information-stealer like Agent Tesla, Loki-bot and others since at least January 2019. The adversaries using custom droppers, which inject the final malware into common processes on the victim machine. Once infected, the malware can steal information from many popular pieces of software, including the Google Chrome, Safari and Firefox web browsers.
The injection techniques we’re seeing in the wild are well-known and have been used for many years, but with the adversaries customizing them, traditional anti-virus systems are having a hard time detecting the embedded malware. In this post, we’ll walk through one of these campaigns in detail and how the different stages of the dropper hide the malware. Any internet user is a potential target of this malware, and if infected, has the potential to completely take away a user’s online privacy.
Technical overview
The campaigns we analyzed started with a malicious email similar to the one below:
Figure 1 – Phishing email
An ARJ archive is attached to this email. ARJ is an early 1990s archive format often used on the pirated software scene to convert files into archives. ARJ can split the archive into multiple smaller files. This made it easier to share these files over dial-up connections. ARJ archives can be unpacked with various tools like 7-Zip or WinRAR. Users can easily find an unpacker by double-clicking on the file and searching in the Windows Store for the appropriate software.
We often see that adversaries use old archive formats, hoping to bypass weak email security gateways. In this case, this archive wasn’t split into multiple files and it contained only a single executable with the name: “IMP_Arrival Noticedoc.exe”. This actor often used filenames with the schema “….exe. In other campaigns by this adversary, we also saw completely different names and different file types like malicious office documents acting as first stage droppers. In this blog post, we will focus on the first ones.
Dropper
Most of the executables are compiled, sometimes UPX packed, AutoIt scripts that can be easily decompiled. Unfortunately, as usual, the content was heavily obfuscated before compilation. Figure 2 shows the decompiled version of the script.
Figure 2 – Decompiled version of the AutoIT script
The deobfuscated version of the AutoIT script in Figures 3 and 4 shows that it comes with some anti-VM checks in the beginning. These checks are very typical for AgentTesla campaigns for years, you can often find them in one or the other form in the first stage droppers.
Figure 3 – Start of the deobfuscated AutoIT script
Figure 4 – VM checks of the deobfuscated AutoIT script
If these checks do not find anything, it is decoding and extracting resource font type (8) names from the string in the first parameter ($data) handed over to the DecodeDataFromPEResourceOrString function (Figure 7). In the GetResourcesFromPE function (Figure 6), this parameter is converted into a string and split into the different font resource names. The result is a list of strings in the following order:
SystemPropertiesDataExecutionPreventionM
Windows.Media.BackgroundPlaybackK
windeployL
LaunchWinAppX
ccaF
CellularAPIQ
MuiUnattendE
RmClientE
ucsvcG
refsutilV
SpeechRuntimeV
DPTopologyAppv2_0N
These font type resources are then extracted from the PE resources and concatenated to a large binary.
Figure 5 – Resource Section of IMP_Arrival Noticedoc.exe
Figure 6 – GetResourcesFromPE Function
The result is stored again in the $data variable (Line 245 in Figure 7) and the order of the stored bytes is reversed by StringReverse(BinaryToString($data)) in Line 246. This is the final payload malware in an RC4 encrypted form. The variable $sopcode contains the bytes of the RC4 code. After preparing the shellcode and the encrypted payload data, the RC4 function is getting executed in line 262 and decrypts the payload.
Figure 7 – DecodeDataFromPEResourceOrString RC4 Function
The following pictures show the disassembled RC4 shellcode:
Figure 8 – RC4 function ($opcode variable)
After the payload is decrypted, the script calls the final InjectPayloadIntoProcess function to inject the payload into another process. It is offering nine different legit process options for this injection. The adversary eventually selects which one will be used by providing the corresponding number to the function.
Figure 9 – Injection victim process selection
In this case, the adversaries picked option one — RegAsm.exe — to hide the payload. The rest of the function is quite similar to what was already described in other blogs. It is preparing the local injection shellcode ($a5_local_shellcode) and executing it in Line 211 in Figure 10. As mentioned before, this code finally hides the payload inside of the selected legit process. The decoded payload is handed over to this injection shellcode as the last parameter ($a4_payload_code).
Figure 10 – Process Injection code of the AutoIT script
The AutoIT script contains several additional functions that are not used in this campaign. For example, functions for the following tasks:
Write a file to the TEMP directory and execute it.
Download a file from the internet and execute it.
Execute a script via the command line.
Privilege escalation.
The AutoIT scripts in the different campaigns are always very similar to the one described above. It usually just differs by how they built the payload. Some scripts extract the payload from the resource section as described above, others have the encrypted payload stored in a large string inside the AutoIT script (Figure 11). The decoding function shown in Figure 7 is more or less the same, but the $rt parameter is set to -1, which means the GetResourcesFromPE function (Figure 6) doesn’t do anything, except returning the unmodified content of the $data variable, or in other words the content of the $payload variable in Figure 11.
Figure 11 – Long String based AutoIT script start
The Injection part of these scripts always work more or less the same, Figure 12 shows an example of another script.
Figure 12 – Long String based AutoIT script injection part
Payload
The injected payload is in many cases an obfuscated version of AgentTesla. The software is capable of stealing credentials from most browsers, email clients, SSH/SFTP/FTP clients and other software. Please see the IOC section below for additional details. It supports exfiltration via SMTP, FTP and HTTP exfiltration. In this case, it only used SMTP. This version is very similar to the one described by Yoroi in the payload section of their blog post, except it is not obfuscated with any obfuscator detected by the latest de4dot. Some functions are also slightly modified or reordered, but most of them are probably done by the obfuscator. We think it is close to the customized Agent Tesla version that’s been circulating online since several months.
Figure 13 – AgentTesla
It is resolving configuration settings and suspicious strings at runtime when they are used. The function shown in Figure 10 is implemented in the executables static class constructor (.cctor). It is using the Rijndael algorithm to decrypt certain large arrays. The offset is picked based on the integer which was handed over to the function. On the right side of the screenshot, you can see the length of the array section in purple.
Figure 14 – Agent Tesla decoding routine
The next screenshot shows the usage at runtime. For example, decoding certain parameters for email exfiltration.
Figure 15 – Agent Tesla string obfuscation
The fully deobfuscated version of the function looks like this:
Figure 16 – Agent Tesla email function (deobfuscated)
This is the typical AgentTesla function used for years. It is interesting that it seems to be that the obfuscator is customized for this Agent Tesla version or vice versa. It looks like it is filling in variables at the time it is obfuscating the original code. In functions that are in this sample, but never used and even in a few used ones, some of the hardcoded strings are filled with variables e.g. %filename%.
Figure 17 – Obfuscator variables
Conclusion
This campaign is another example of what modern malware uses to fly under the radar. With the process we’ve described in this post, the actors can hide the original malware inside the dropper. The malware is only decrypted at runtime and injected into memory — it’s never unencrypted on the hard drive. The adversaries use complex droppers that leverage several different obfuscation techniques to make it as hard as possible for antivirus programs to detect the malware. By using these droppers, they can quickly and easily change the final malware for their campaigns. Even known malware is often successfully hidden against anti-virus systems by using these kinds of obfuscation chains.
Coverage
Ways our customers can detect and block this threat are listed below.
Advanced Malware Protection (AMP) is ideally suited to prevent the execution of the malware detailed in this post. Below is a screenshot showing how AMP can protect customers from this threat. Try AMP for free here.
Cisco Cloud Web Security (CWS) or Web Security Appliance (WSA) web scanning prevents access to malicious websites and detects malware used in these attacks.
Email Security can block malicious emails sent by threat actors as part of their campaign.
Network Security appliances such as Next-Generation Firewall (NGFW), Next-Generation Intrusion Prevention System (NGIPS), and Meraki MX can detect malicious activity associated with this threat.
Threat Grid helps identify malicious binaries and build protection into all Cisco Security products.
Umbrella, our secure internet gateway (SIG), blocks users from connecting to malicious domains, IPs, and URLs, whether users are on or off the corporate network.
Additional protections with context to your specific environment and threat data are available from the Firepower Management Center.
Open Source Snort Subscriber Rule Set customers can stay up to date by downloading the latest rule pack available for purchase on Snort.org.
IOC
Agent Tesla Stealer capabilities found based on decoded strings:
7Star Browser
Amigo Browser
Apple Keychain
Becky! Internet Mail
Brave Browser
Centi Browser
Chedot Browser
Chrome Browser
Chromium Browser
Citrio Browser
Claws Mail
CocCoc Browser
Comodo Dragon Browser
CoolNovo Browser
Coowon Browser
CoreFTP
Cyberfox Browser
DynDNS client
Elements Browser
Epic Privacy Browser
Eudora Mail
Firefox Browser
FlashFXP FTP client
Flock Browser
Foxmail
FTPCommander
FTPGetter
FTP Navigator
i360 Browser
IceCat Browser
IceDragon Browser
IE/Edge Browser
Incredimail
Internet Download Manager
Iridium Browser
JDownloader
Keylogger
K-Meleon Browser
Kometa Browser
Liebao Browser
Mozilla SeaMonkey
Netgate BlackHawk Browser
NoIP DNS client
Open VPN
Opera Browser
Opera Mail
Orbitum Browser
Outlook
Pale Moon Browser
Paltalk Video Chat
PassWd
Pidgin
PocoMail
QIP Surf
QQ Browser
Safari Browser
Screenshots
Sleipnir 6 Browser
SmartFTP
Sputnik Browser
SRWare Iron Browser
TheBat! Email client
Thunderbird
Torch Browser
Trillian
UC Browser
uCozMedia Uran
Vivaldi Browser
WaterFox Browser
Wi-Fi Credentials and Profiles
Windows Credentials
Windows Domain Certificate Credential
Windows Domain Password Credential
Windows Extended Credential
Windows Generic Credential
Windows Secure Note
Windows Web Password Credential
WinSCP
WS_FTP Pro FTP client
Yandex Browser
Email: Email: [email protected] Mailserver: mail.casadavilas.com
Malware moved to: C:UsersDex DexterAppDataLocalTemptmpG766.tmp [%TempPath% + “tmpG” + DateTime.Now.Millisecond + “.tmp”]
Hashes executables: d076ed9b31172c37a0d6bafae0c18d559f62453f52c17d41dc2e24fd55a91e4a 1c46332d2a0ab693ed1086f8ee78df47798361b4156619e2488cbb6851063373 003ee7d88f3a04cfc1b96744b060170d80da75589c67deaf65adb02d45616bb5 16f9a14d045fa28708710b5a089e1d1a361c8f5702a8574989b1935072c14a1d 4030b864bcff5bd617e3be273387eec3857b019d20b59c8f2f0710f1b1876ede 5246d87a5a69e7d50e7475bda5f9a74c3585188f0c937fcebebdf168043decd7 59880d4c59643d7b268082696931dcbe966780eef072f1150d1ac65dbc95d222 651c520971bc931dc3760b077a8ecd2fd3a7e4535afe2f0fd208168dc2a501e1 694dcad0105052b3b74678a9c0e4ad3c17e8a3e87314863751296d58aa263b23 a758516e200a5afb49ab2082c433fa59a8dbe2cf28973da6691a74759de479e1 b61a6d30e268a406f52aca04cc2a82853968f3516e38d2b5522e9fa5d4c0d3f5 e1954e26d6e82da6906441f30d133ad56b0154777128278d355365da475c4db4 F7303285a2039ab934b696fec43e54fc5c8ab5c6332c62a78891da71f3c2fb82
ARJ files: 667519d5fea7b6137de2845dc900cf2813c8fd8c8476b107fe9a281e7aa5248d 198dcc8511236212410e248d66c86236e1f23a79459a4c61aca5c8b913c9539c
Related hashes: 09dbe016c180e28b748f932805fc35170e348f3201d6939fc2b8368466c69315 10739410391018cedb2bdf6804c4506ea256695935afc34be786894e5cc80602 176d4d6ef5adb9655f63931914fe06688418d6ce62a3bbe6d6f09ccad53cca2f 4059c87e8d39f69e1fb3bc5d094af1dafca73e8b662eb8d6bb850bfb10d1e92e 421a642d23630ee480094dcb51f6ad6dc2430015d54cddbe0dbf299ee26869d4 51aa560a3709127d26dfb9289ec7d9b020558a0ad33b638bbddfaab6b180d7c3 61ee8edf4e9241ac3f5922547577e2c9b6a589b7402845be68c9e4bf377143b4 754fcf3ef2216f15750393c9ee580d1de9bb8b5834532183a7ef09a109b3990f 7a611fac9133845b29b73be71d1e08f2a82ee04a470b11bb0a25692da7c8caed 82ef16248078738591cc548e611a8ce22cb6b30db3ce123bd2900b0ddf644dba 94c3bbcf5af25417b755d9168cf6146b2de52658d8b909e0cdc38efde98df9fc 96bad87dae87cb2c73ce0e2f092dc68adc02a09cc2f549d1a4f390e42c41bf08 a2b174b1679d1a508c70acd2626e297c85aee3da5d50b5a0c7388960b6085c4a a5ddd6719e9ced4f18289103a47bf39ad0e221fcac7ce00ed8e7180865b3c63a aa295b39e3c9fbae2370bfc3bc03528a13fe5ee30d3497fff053fd4ab2ba790f b7d790f4e11364d50c32a0a36fe7c9e159073c905fb4462c8d95e31ea608ede5 be7edfa65d420d6210b5e488b25ffe8a4fc1c37f9f358de97e0915d535766e74 d5cd5875253dbabb6548d96a290e73d196f6db250af8c3ec316d855ef7660f5a da5d248dc77bd464c25fe5ad21ca62e58c69c4cc10cf27a13985432acfa6fd39 ddee0696d2062e1706c368c5066392d56e804c707d6923397cf66d56d2016773 de8fdea527ec9751531f15e727a7221103c5158bf14651faf19e648ec9652a0f e480512a207fc9809035b273dd6c35fcd6caf8829ce5b9d81cc82f2d3b2d5394 e4b55be3eccbac57200e1c5e56d324afa23fdb8b12aba8d5be235b083b5afe0d f05329ffcf221c72570e214a62fb8f04633c8d9e405a4278fd9360e738d9d779 f39c3cea5b1edcc71db1eb140b21f2aa56d9aee87c6d77528b84697aa9b19739 f6f35c3cbf83450d1fecb7101784e6cc89fa13b994ae16199087c2c5119984d3 fc2e81038c1cf19c40b9586889197446b426e8e4ed208931a616d838448fdd23 fc7cf41f41bb94253d946d5db29d65697464772af341e9a2bb20dffb943e716e fe56eb80eb5b119b5c4e56811592029c4d8674061d4fbe89f8174cc4b403cfbf
URLs: hxxp://premacorceb[.]com[/]drug[/]five[/]fre.php hxxp://www[.]ibsensoftware[.]com/
IPs: 194[.]147[.]32[.]237 194[.]58[.]111[.]187
#gallery-0-5 { margin: auto; } #gallery-0-5 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-5 img { border: 2px solid #cfcfcf; } #gallery-0-5 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Custom dropper hide and seek Original Post from Talos Security Author: Executive summary Most users assume they are safe when surfing the web on a daily basis.
0 notes
Text
How Does Search Encrypt Work?
Search Encrypt is a private search engine designed with privacy as its core value. Search Encrypt protects your privacy by encrypting your search terms, expiring your browsing history and using advanced SSL encryption. We’re sharing a bit about how we encrypt your searches and, as a result, protect your privacy.
What Happens When You Search with Search Encrypt?
Search Encrypt checks the URL of each website you visit. We do not log or store that data anywhere.
For your privacy, Search Encrypt intercepts the requests if it’s on our list of sites that may track your searches.
Search Encrypt encrypts your search locally using industry standard AES-256 encryption.
Your locally encrypted search term is securely transmitted to our servers.
To provide you with the most relevant results possible, we then decrypt your search term and securely request results from our search & content partners.
We aggregate the most relevant results and securely display them to you.
For added security, your local browsing history, for any search we protect, expires and goes away after 15 minutes of inactivity.
Search Encrypt Redirects Tracked Searches
Search Encrypt checks if you are using a search engine that tracks you. If it sees that you are being tracked, it encrypts your search term locally and then transmits it securely to our servers. We then decrypt and redirect your search term through our private search engine. This protects your privacy by not allowing the searches on major search engines to go through. Our browser extension adds a layer of protection by helping you move away from search engines that track you around the web. You may be using one of those search engines without even knowing. We then provide you with the most relevant results possible by securely requesting and aggregating them from our search partners.
Search Encrypt’s Encryption Methods
Encryption happens when an algorithm scrambles your data into an unrecognizable “cipher” form. An encryption key is then required to view the data in plain text. There are many types of encryption. Search Encrypt uses AES, which is the most widely used encryption algorithm. AES-256, which has a 256-bit cipher key, is used by the NSA for TOP SECRET classified information.
AES-256 Encryption
AES, Advanced Encryption Standard, is a data encryption standard endorsed by the National Institute of Standards and Technology (NIST). It replaced the previous standard, Data Encryption Standard, DES. AES is a more secure system for internet communications and transactions. Two Belgian Cryptographers, Joan Daemen and Vincent Rijmen, created AES in October 2000. The system was originally called Rijndael before being accepted as the new encryption standard, AES. Rijndael offered security, performance, efficiency, implementability, and flexibility beyond that of any of the other candidates for the new encryption standard.
Some well-known uses of AES include Signal Protocol, used in Google Allo, Facebook Messenger, and WhatsApp. The technology is also used in certain game engines, like Rockstar’s Advanced Game Engine used in Grand Theft Auto IV to deter hacking in online multiplayer game modes. AES-256 denotes that the encryption key size is 256 bits. AES supports 128, 192 and 256-bit key sizes. 256 bit keys mean that there are 2256 options for encryption keys. The number of options is bigger than the number of atoms in the perceivable universe. In other words, no person, or computer, will be able to “guess” the key. With current computing capabilities, cracking a key of this length would take millions of years.
SSL (Secure Socket Layer) Encryption
Secure Socket Layer, SSL, is a cryptographic protocol that encrypts communication on a computer network. It allows for secure transfer of sensitive information like financial info, passwords or Social Security numbers. Websites that process payment via credit card must have an SSL certificate.
SSL works by creating a public and a private key. These two keys then create a secure and encrypted connection. Websites with SSL certificates communicate with the user’s browser to let it know that a secure connection is available. Without SSL encryption, sites transmit user information in plain text. This means that anyone with access to the network could theoretically access the data. SSL encrypts this data so it can’t be easily leaked or hacked.
Expiring Browsing History
Beyond the traditional encryption methods, we use a short lived key for client side encryption of search history. This means that you, or anyone with access to your computer, can’t access your search history after you finish searching. Because we use an expiring key, your search history is totally gone, even if a hacker accesses the encryption key.
Privacy-Friendly Token
When you come to Search Encrypt’s site for the first time, we give you a token that is associated with your IP address. We don’t track or store your IP address, and we don’t link your searches to your IP address. The token can only be seen by Search Encrypt and you. The purpose of this token is to let us encrypt your search term and to let you see your search results in non-encrypted form.
Search Encrypt’s token logic works to let us know when it’s you searching so we can let you view your results. If the token is not present, your searches stay encrypted so no one else can view them.
Perfect Forward Secrecy
Search Encrypt offers perfect forward secrecy. This is any encryption method in which a breach of the long-term key doesn’t compromise past session keys. Your search terms are encrypted and not linked to any personally identifiable information. For our users it offers a sense of security, because even if the NSA or hackers were able to access our servers, we store none of your information. Through a combination of advanced encryption, expiring browser history, and not storing user information, Search Encrypt delivers a secure and private search experience.
Search Encrypt vs. Other Search Engines
Most search engines track your searches. Search Encrypt doesn’t track any personally identifiable data.
Other search engines use your personal information to serve you targeted ads around the internet. Search Encrypt serves ads on its results page only, and they are based on you search term and nothing else!
Search Encrypt uses end-to-end encryption so your search terms aren’t as vulnerable to hackers who otherwise could see what you were searching for.
Search Encrypt uses AES-256 encryption combined with expiring encryption keys which mean your search terms disappear after you’re done searching.
Why Should You Use a Private Search Engine, Like Search Encrypt?
Private search engines don’t track you.
You can keep other people from seeing your search history.
Private search engines can’t follow you around the internet with ads.
Your data can’t be hacked or leaked if your search engine never collects it.
Read More about the importance of private search engines.
#search encrypt#search engine#privacy#how does it work#blog#article#search#google#duckduckgo#startpage#searx#technology#private internet#digital privacy#digital#tech
0 notes
Text
Communication Protocols
MQTT Protocol:
The Communication protocols used for transfer of data between the master node and the smart band here is the MQTT protocol. MQTT stands for MQ Telemetry Transport. It is a publish/subscribe, extremely simple and lightweight messaging protocol, designed for constrained devices and low-bandwidth, high-latency or unreliable networks. The design principles are to minimize network bandwidth and device resource requirements whilst also attempting to ensure reliability and some degree of assurance of delivery. These principles also turn out to make the protocol ideal of the emerging “machine-to-machine” (M2M) or “Internet of Things” world of connected devices, and for mobile applications where bandwidth and battery power are at a premium. As of March 2013, MQTT is in the process of undergoing standardization at OASIS. The protocol specification has been openly published with a royalty-free license for many years, and companies such as Eurotech (formerly known as Arcom) have implemented the protocol in their products.
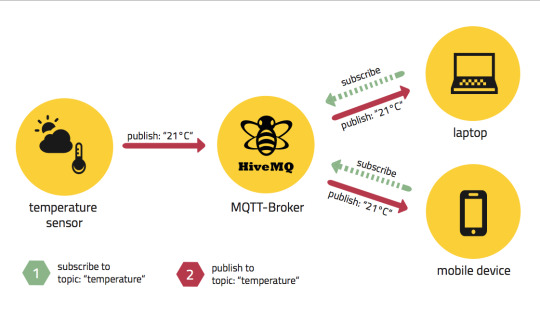
Security:
You can pass a user name and password with an MQTT packet in V3.1 of the protocol. Encryption across the network can be handled with SSL, independently of the MQTT protocol itself (it is worth noting that SSL is not the lightest of protocols and does add significant network overhead). Additional security can be added by an application encrypting data that it sends and receives, but this is not something built-in to the protocol, in order to keep it simple and lightweight.
Advanced Encryption Standard (AES) protocol:
The Advanced Encryption Standard (AES) is a specification for the encryption of electronic data established by the U.S. National Institute of Standards and Technology (NIST) in 2001.
AES is a subset of the Rijndael cipher developed by two Belgian cryptographers, Vincent Rijmen and Joan Daemen, who submitted a proposal to NIST during the AES selection process. Rijndael is a family of ciphers with different key and block sizes.
For AES, NIST selected three members of the Rijndael family, each with a block size of 128 bits, but three different key lengths: 128, 192 and 256 bits.
AES has been adopted by the U.S. government and is now used worldwide. It supersedes the Data Encryption Standard (DES), which was published in 1977. The algorithm described by AES is a symmetric-key algorithm, meaning the same key is used for both encrypting and decrypting the data. This protocol is not used in the project because it is little slower than MQTT protocol and we need is the real time processing and very fast end to end transfer of data.
0 notes
Text
Encryption Algorithms
Encryption Algorithms
In our previous blog post ‘Encryption‘ wherein we explained encryption and different encryption methods. This blog post is subsequent to that and here we will explain different types of encryption algorithms that are most commonly used in cyber-security world.
Types of Encryption Algorithms
Tripe DEC/DEC
RSA
AES
Blowfish
Twofish
MD5
SHA1
HMAC
Triple DES or DES/3DES
Data Encryption Standard was first used and endorsed by US Government in 1977. DES encryption algorithm forms the basis for ATM PIN authentication and also utilized in UNIX encryption password. DES is a block cipher with 64-bit block size and uses 56-bit keys.
Triple DES or 3DES was designed as a more secure and stronger encryption algorithm to replace the original version of DES algorithm. Triple DES encrypts the data three times with three different individual keys of 56-bits each, which makes the total cumulative key length up to 112-168 bits long.
RSA
RSA is a public-key encryption algorithm and a standard for encrypting sensitive data sent over an insecure network like the Internet.
RSA encryption algorithm was first introduced by Rivest, Shamir and Adleman at Massachusetts Institute of Technology in the year 1977. It is with reference to these three individuals that this method of encryption was named as RSA (Rivest-Shamir-Adleman).
RSA, a public-key cryptography, is an asymmetric encryption which uses two different but mathematically linked keys for encryption and decryption. In RSA encryption algorithm, a public-key is used for encryption and a private-key for decryption. The public-key could be shared with others but the private-key must always be kept secret.
RSA is one of the most popular and widely used encryption algorithm for encryption and digital signatures in the cyber-security world today.
AES
AES or Advanced Encryption Standard is an encryption algorithm that was announced and approved by the United States National Institute of Standards and Technology (NIST) in November 2001. AES replaced DES encryption algorithm and became a standard encryption technique for the US government in 2002.
AES encryption algorithm was developed by two cryptographers from Belgium, Joan Daemen and Vincent Rijmen, who submitted it to NIST where it was approved. AES, originally named Rijndael, is a family of ciphers with different key and block sizes.
AES encryption algorithm comprises of three block ciphers of 128-bits, 192-bits and 256-bits. Although encryption with AES 128-bits is quite strong and efficient, 192-bits and 256-bits key is used for higher grade of encryption.
AES is a symmetric encryption algorithm and uses a single private-key for both encryption and decryption processes. AES encryption algorithm is used by numerous organizations worldwide apart from being trusted by the US government.
Blowfish
Blowfish is a symmetric block cipher that was developed and introduced by Bruce Schneier in 1993 as an alternative to the encryption algorithms existing at that point in time.
Blowfish has a 64-bit block size and a variable key length from 32-bits up to 448-bits. Blowfish encryption algorithm splits a message into the blocks of 64-bits and then encrypts the blocks individually.
Blowfish is unpatented and a free to use encryption algorithm, easily available in the public domain.
Twofish
Twofish is a block cipher encryption algorithm based on Blowfish encryption algorithm. Twofish was one of the five finalists at NIST to replace DES encryption algorithm where NIST eventually selected and standardized the Rijndael algorithm, commonly known as Advanced Encryption Standard (AES) algorithm.
Twofish is a symmetric key block cipher with a block size of 128-bits and key size ranging from 128-bits to 256-bits. Twofish algorithm being a symmetric encryption technique uses a single key for encryption and decryption.
Twofish encryption algorithm was designed by a team of cyber-security experts led by Bruce Schneier at Counterpane Labs in the year 1998. Like Blowfish, Twofish is also unpatented, license-free, free-to-use and available in public domain.
MD5
MD5 Algorithm was developed by Professor Ronald L. Rivest of MIT in 1991, and is widely used to verify data integrity. MD5 is a one-way hash function which creates a 128-bit hash value, and is most commonly used in digital signature applications.
MD5 algorithm has been optimized for 32-bit machines and was designed to replace MD4, an earlier hash function also designed by Rivest.
MD5 algorithm verifies data integrity by processing a variable-length message into a fixed-length output hash of 128-bits. MD5 algorithm is sometimes also referred to as Message-Digest algorithm.
SHA
SHA or Secure Hash Algorithm is a family of cryptographic functions which includes SHA-0, SHA-1, SHA-2 and SHA-3. SHA algorithms are component of SSL certificates to verify data integrity, that is to ensure that the data has not been modified.
SHA-1 cryptographic hash function that was designed by the United States’ NSA in 1995. However, SHA-1 is no longer considered to secure enough and post 2010 many cyber-security experts have recommended the use of SHA-2 or SHA-3 as a replacement to SHA-1. Most of the popular browsers would stop the support for SHA-1 based SSL certificates.
SHA-2 is also designed by NSA and was first published in 2001. SHA-2 is a set of cryptographic hash functions which includes six hash functions of different digest sizes: SHA-224, SHA-256, SHA-384, SHA-512, SHA-512/224, and SHA-512/256.
SHA-3, formerly named Keccak, was designed by cryptographers Guido Bertoni, Joan Daemen, Michael Peeters, and Gilles Van Assche and was approved by National Institutes of Standards and Technology (NIST) as a part of a competition which received 64 submissions from all over the world. Subsequently, SHA-3 standard was released by NIST in August 2015.
HMAC
HMAC or Hash-based Message Authentication Code (HMAC), first published in 1996, is a type of message authentication code that involves both a secret cryptographic key and hash function. HMAC simultaneously verifies the data integrity and authenticates the message.
In HMAC, the message and the key are hashed in separate steps which adds to the security of HMAC. The cryptographic strength of HMAC is dependent on the strength and size of the hash function and size of the key.
IPSec and TLS protocols use HMAC-SHA1 and HMAC-MD5 algorithms.
- Captain Krypto
Kryptotel is an IT Security Services and Product Development Company specializing in Cyber Security and Secure Communications. Kryptotel develops secure communication applications with strong encryption and security features. Feel free to consult Kryptotel for your cyber-security challenges. www.kryptotel.net.
- See more at: http://learning.kryptotel.net/encryption-algorithms/#sthash.IKxROwR7.dpuf
0 notes
Text
Original Post from Security Affairs Author: Pierluigi Paganini
One of the latest trends for the attackers is to leverage the ISO files to avoid detection, the technique has also been used in a recent Hawkeye campaign.
Introduction
As we described in our previous post, one of the latest trends for the attackers is to leverage the ISO files in order to reduce detection chances. This technique has also been used by a recent Hawkeye spreading campaign.
“Hawkeye Keylogger” is an info-stealing malware for sale in the dark-web. Anyone can easily subscribe to the malware service by paying a fee. It has been in continuous development at least since 2013 and the malware authors behind Hawkeye have improved the malware service adding new capabilities and techniques. It can collect credentials from various applications, mostly email clients, web browser and FTP clients, and send them to the crooks via various protocols such as FTP, HTTP, and SMTP.
So, our Cybaze-Yoroi ZLAB decided to take a look at this recent Hawkeye attack, tacking its anti-analysis protection and the anti-debugging techniques enforced by the Visual Basic packer used by the crooks.
Technical Analysis
The delivered file is an ISO image. Inside of it, there is a bat file, but actually is a well formed PE file. So, we can extract the “bat” file and replace its extension in “exe”.
Figure 1: Fake .bat file inside the ISO archive
Hash 32951a56e3fcd8f5b006c0b64ec694ddf722eba71e2093f7ee90f57856941f3d Threat Hawkey Spyware Brief Description Hawkey Spyware inside a Visual Basic Packer Ssdeep 12288:GVwYvwrMkE9LfRUXkpW7zGidwY/rwxOp8mH:COrI9zRUJfGCfzw0
Table 1: Information about the PE file inside the ISO image
The ISO file has low AV detection rate, but only by extracting the executable from the ISO image, the rate raises:
Figure 2: AV Detection of the ISO compressed file (left) and of the extracted file (right)
The PE file is packed with a Visual Basic 5.0 stub. It has the duty to protect the core of the malware and complicate the analysis:
Figure 3: Visual Basic packer evidence
As seen above, the malware is written in Visual Basic 5.0. So it is possible to decompile the malware through the use of the ad-hoc decompilers.
Figure 4: Visual Basic code decompilation in P-Code
The decompiled code has been translated in P-Code and it is quite obfuscated in the same way. The only solution to obtain more information about the infection mechanisms is to debug the program.
The first trick to complicate the analysis is to dynamically create a new memory section where inject some code, through the use of the “VirtualAlloc” function. The malware decodes some a piece of code, and choose a random new virtual address space to alloc memory, in this case “0x00260000” loaded into the EAX register.
Figure 5: Memory allocation through the VirtualAlloc API
The GetTickCount Anti-Debug Technique
After the context switch inside the new allocated area, the malware adopts the well known “GetTickCount()” anti-debug technique. According to the MSDN documentation, GetTickCount retrieves the number of milliseconds that have elapsed since the system was started, up to 49.7 days. This API call is used by the malicious actors to retrieve the time of the execution of the process, and if it is higher than a preset threshold, the malware terminates its execution:
Figure 6: GetTickCount routine a new address space
The first malicious action of the created address space is the invoking of the GetTickCount API and the result is:
Figure 7: GetTickCount result in EAX register
The result of the GetTickCount function is stored in EAX register. After doing some other decrypting operations, the malware invokes it another time.
Figure 8: GetTickCount subtraction anti-debug trick
After the second invocation of GetTickCount, there is immediately the subtraction of the two values and it is placed in EAX register. The next instruction is a comparison between the EAX register and a preset threshold value, “0x5DC”, which is 1500 in decimal representation. According to the Microsoft documentation, the resolution of the GetTickCount function is 10ms, thus we can deduce that the decided threshold by the cyber criminal is 15 seconds. After understood the trick, it quite easy to bypass and go on to analyze the sample.
Figure 9: ShellExecute routine to run the payload
The malware allocates another memory space to write an entire file with the MZ header and it is opened through the “ShellExecute” API function. Dumping the process in this moment, another piece of code hidden in a resource, which did not exist before the anti-debug trick, emerges:
Figure 10: Resource comparison between the original exe and the self-modified exe
As shown in the above figure, the original file (on the left) presents as resources only the icons and the manifest, instead the self-manipulated file presents a resource called “RCData” with a resource named “__”. It is the encrypted final payload.
Figure 11: Malicious resource retrieving routine
In order to protect itself and to make more difficult the analysis, the malware respawns itself through the “CreateProcessInternalW” API call:
Figure 12: Execution routine of the final payload
Now the real payload is ready to be self-decrypted with a custom internal routine.
Figure 13: Decoding routine of the final payload
After the decryption routine, the malware copies this new code into another piece of memory through the “memcpy” function. Moreover, in order to validate the correct extraction of the payload, the malware checks if the first two bytes of the memory spare are “0x5A4D” which is “MZ” in ASCII code.
Figure 14: Validation check of the correct decoding of the final payload
Dumping the file, the real payload is unveiled.
The Payload
The extracted payload is a PE file compiled in .NET C# language with the following static information:
Hash a3aa6e220591f05f4e2ecc4f4741ac6b6715ebb2b5c42c2b7bb52142c54be30b Threat Hawkey Spyware Brief Description Hawkey Spyware obfuscated payload Ssdeep 6144:HuXT5iKKhhSHCMA2g22fB1YbcLetS7iz+K3hk:OXtxc/r1fXrwgil3h
Table 2: Static information about the final payload
The payload sample is obfuscated with the .NET Reactor tool, but the cleared version can be easily restored:
Figure 15: Usage of .NET Reactor obfuscator evidence
Below some static information of the final payload is reported:
Hash a848c84a1306ea7cc4704eced4067db1012c0bf1b9b65f8c04a8379d71464eaa Threat Hawkey Spyware Brief Description Hawkey Spyware clear payload Ssdeep 6144:37iz+K3hkCAg3JhmkuEFZ+1WjsroyGh0DBabr:Lil3hdhmOF
Table 3: Static information about the cleared version of the final payload
Due to the fact that the payload is written in .NET framework, it is possible to debug the code in order to retrieve all the details of this new sample. The debugging of the sample lets emerge the attribution of the malware, HawkEye.
Figure 16: Recurrent string decryption routine through the usage of Rijndael algorithm
Every sensitive information, string or other information is encrypted through Rijndael algorithm, as shown in figure 16. Before starting any operation, the malware tries to make a simple evasion trick. It retrievers the username of the victim machine and it compares this one with a series of usernames hardcoded. These usernames are the classical ones adopted by the sandboxes and if one of them is matched, probably the malware is run inside a virtual machine.
Figure 17: Sandbox evasion trick
After the simple check, the info stealer starts to perform its malicious operations. The first malicious operation is the persistence mechanism adopted by the malware:
Figure 18: Persistence mechanism
The persistence is guaranteed through the setting of the classic registry key “HKCUSoftwareMicrosoftWindowsCurrentVersionRun” with the value “C:UsersAdminAppDataRoamingMyAppMyApp.exe”, having already copied itself in this path. However, it’s important to say that if the malware is launched from the original wrapper, it copies in the “MyApp” path the entire executable, because the payload is executed inside the wrapper process as a thread; instead if only the final payload is executed, only this part is stored.
Figure 19: Task Manager disabling
A particular auto-protection mechanism adopted by the malware is the disabling the possibility to open the Task Manager process from the user, through the setting of the highlighted registry key in the Figure 19. At this point the malware can start the information stealing routines.
Figure 20: Password retrieving routine from Internet Explorer
The first information retrieved is the password stored inside Internet Explorer through the routine described in the above figure. This is only the starting point: it retrieves all sensitive data and login data from a large list of browsers. A little example is shown in the following figure:
Figure 21: Piece of the browser list harvested by the malware
Below, the complete list:
Google Chrome
Yandex
Comodo Dragon
Cool Novo
Chromium
Torch Browser
7Star
Amigo
Brave
Cent Browser
Chedot
Coccoc
Elements Browser
Epic Privacy
Kometa
Orbitum
Sputnik
Uran
Vivaldi
UC Browser
Flock Browser
In the same way, the malware looks for other credentials coming from other services, like CoreFTP, FileZilla and JDownloader. The last information stolen by the malware is the registered email accounts on the victim machine. The searched email clients are:
Outlook
SeaMonkey
Postbox
Thunderbird
Now, we wanted to deepen the password gathering routine of the malware on the Microsoft Outlook application. So, we created a fake account and we logged on the Microsoft email account software.
Figure 22: Registry key where it is stored the Microsoft Outlook client user configuration
Themalware retrieves a particular registry key: “HKCUSoftwareMicrosoftWindows NTCurrentVersionWindows Messaging SubsystemProfilesOutlook”. Inside of it is stored the configuration of the Microsoft Outlook user profile.
Figure 23: Outlook password decryption routine
The method “smethod_50” in figure 23 shows how is simple to decrypt the password saved in that registry key: it is enough retrieve the array of bytes and use it as parameter, together with the CurrentUser DataProtectionScope, to the static method provided from the .NET framework, “ProtectedData.Unprotect()”. After that, the harvested information are collected in a list, ready to be sent to the server.
Figure 24: Creation of the list of the gathered accounts
The last action is properly the preparation to send the information to the recipient. As the classic HawkEye malware, the communication protocol designed to transmit the stolen info is SMTP. For this reason the malware needs to use the API provided by the .NET framework in order to instantiate an SMTP client. Debugging until the right point, the malware configuration are revealed:
Figure 25: SMTP client account configuration
Conclusion
Hawkeye is nowadays a well known threat. The security firms analyzed in an excellent way the malware and all the infection chain, but this sample, like our latest ones, has the peculiarity to be protected by a complex and evasive packer.
In the last two posts we saw a tough Delphi packer to analyze, but also this one has some points to analyze that make challenging the reverse engineering process for the analyst. In the end, we were able to dissect all the malware chain revealing the threat actor exfiltration address.
Further technical details, including IoCs and Yara rules are reported in the analysis published on the Yoroi blog:
https://blog.yoroi.company/research/anti-debugging-techniques-from-a-complex-visual-basic-packer/
window._mNHandle = window._mNHandle || {}; window._mNHandle.queue = window._mNHandle.queue || []; medianet_versionId = "3121199";
try { window._mNHandle.queue.push(function () { window._mNDetails.loadTag("762221962", "300x250", "762221962"); }); } catch (error) {}
Pierluigi Paganini
(SecurityAffairs – anti-debugging, malware)
The post Anti-Debugging Techniques from a Complex Visual Basic Packer appeared first on Security Affairs.
#gallery-0-6 { margin: auto; } #gallery-0-6 .gallery-item { float: left; margin-top: 10px; text-align: center; width: 33%; } #gallery-0-6 img { border: 2px solid #cfcfcf; } #gallery-0-6 .gallery-caption { margin-left: 0; } /* see gallery_shortcode() in wp-includes/media.php */
Go to Source Author: Pierluigi Paganini Anti-Debugging Techniques from a Complex Visual Basic Packer Original Post from Security Affairs Author: Pierluigi Paganini One of the latest trends for the attackers is to leverage the ISO files to avoid detection, the technique has also been used in a recent Hawkeye campaign.
0 notes